
Imaging Apple Silicon Macs: A Modern Forensic Guide
Apple’s presence in both personal and enterprise environments continues to grow. As of 2024, macOS holds over 20% of the global desktop OS market share, with adoption in U.S. businesses climbing toward 25%, according to research from IDC and StatCounter. This rise means that Apple devices are increasingly showing up in digital forensic investigations—not just in criminal cases, but also in corporate investigations and eDiscovery.
But these aren’t the Macs of the past. Apple Silicon-based Macs (starting with the M1 chip in 2020) have introduced a radically new system and security architecture. As a result, forensic acquisition techniques that worked on Intel-based Macs or Windows systems are no longer valid—or even possible. Properly imaging a Mac today means understanding these new realities, or risking incomplete evidence collection and inaccurate reporting.
Understanding Apple Silicon’s Security Model
Imaging a Mac properly starts with understanding how Apple has reengineered security from the ground up. Apple Silicon integrates hardware and software protections that are deeply intertwined with the operating system and file system.
Software-Level Security
Modern Macs automatically encrypt all data at rest, whether FileVault is enabled or not. This encryption is tightly bound to the hardware and managed by cryptographic keys stored in the Secure Enclave. Enabling FileVault encrypts the user data volume, requiring valid authentication to decrypt it.
System Integrity Protection (SIP) restricts changes to system files, even by root. In addition, the Signed System Volume (SSV) ensures the integrity of the macOS system volume by verifying cryptographic signatures at boot time. This volume is mounted as read-only, separating system files from user data. These design changes prevent any process—including forensic tools—from making unauthorized changes or accessing protected areas without proper credentials.
Hardware-Level Security
At the heart of Apple Silicon security is the Secure Enclave, a separate coprocessor built into the chip. It handles all cryptographic operations and securely stores encryption keys, biometric data, and authentication tokens. Importantly, it ensures that without the user’s password, access to encrypted data is blocked—there are no shortcuts.
Why the Password is Non-Negotiable
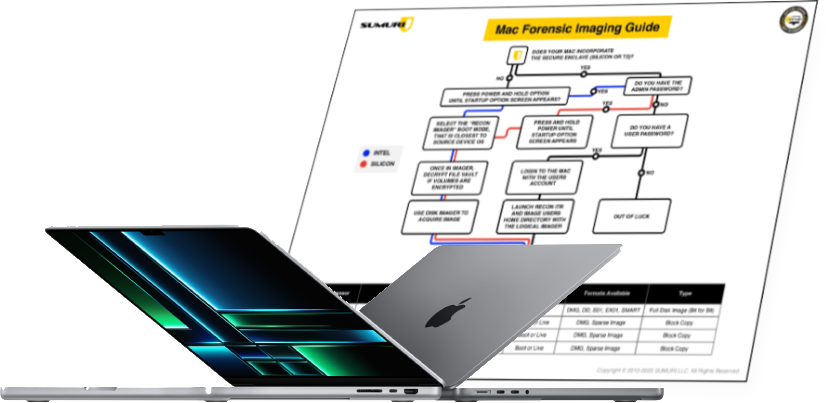
On Apple Silicon Macs, a valid user password is required for any forensic imaging approach. Whether using a bootable forensic environment, live imaging, or Share Disk Mode, authentication is mandatory.
This means investigators must plan ahead. In corporate investigations, arrangements to obtain admin credentials should be part of standard operating procedures. In criminal or civil cases, this may require legal mechanisms such as subpoenas or search warrants that compel password disclosure. Without the password, you won’t be able to decrypt the data, and imaging attempts will be incomplete or unusable.
Forensic Imaging Options on Apple Silicon Macs
There are currently three practical methods for imaging these systems, each with specific technical and procedural implications.
Bootable Forensic Environment
This method uses a macOS-based forensic operating system—such as SUMURI’s RECON ITR—booted from an external drive specifically designed for forensic acquisition.
A common misconception is that you can still perform full physical disk imaging on Apple Silicon Macs. You cannot. Due to Apple’s volume-based design and encryption structure, full physical disk access is no longer available. Instead, once authenticated with an admin password, RECON ITR provides two imaging options: the Container Disk and the Data Volume.
The Data Volume is the primary read-write area of the file system and contains the bulk of user and system-generated data. The Container Disk includes the Data Volume along with additional volumes—such as the System volume and Preboot volume—which are typically read-only or encrypted. RECON ITR offers both options to give examiners flexibility: imaging just the Data Volume for targeted investigations, or the broader Container Disk to examine the complete volume structure, even if some components are not directly accessible by the user to store or hide data.
It’s also important to note that RECON ITR does not require any changes to the system’s security policy in Recovery Mode. This simplifies deployment and ensures that system integrity is preserved. Imaging in this manner allows for the most accurate and complete acquisition possible using macOS-native tools, while preserving Apple’s proprietary metadata and extended attributes critical to forensic analysis.
Live Imaging
Live imaging occurs while the system is running, typically with the user already logged in. This may be appropriate for corporate investigations or situations where speed and minimal disruption are key.
However, live imaging presents a major limitation: you can only access data available to the currently logged-in user. This means that without admin credentials, access to system-level files, protected user directories, or certain metadata may be restricted.
When admin credentials are available, Mac-native tools can be used to elevate privileges and gain broader access. Still, live imaging has inherent risks—it can alter system state, miss deleted data, or cause timestamp updates. Forensic practitioners must balance convenience with potential evidentiary impact and ensure thorough documentation of the process.
Share Disk Mode
In Share Disk Mode, the Mac is booted into macOS Recovery and its internal drive is shared over a network connection—typically using the SMB protocol—to a second Mac for imaging.
While it may appear convenient, this method is extremely slow and unreliable. It establishes a network share between two Macs and is not designed for large-scale data acquisition. Connections are prone to timeouts and drops, making this option poorly suited for forensic-grade evidence collection.
It also requires password authentication to mount and decrypt the target volumes, just like the other methods. Share Disk Mode is best reserved for very limited, low-volume data transfers—not for full forensic imaging.
Why the Imaging Format Matters: Avoiding Metadata Loss
Legacy forensic formats like .E01 or .Ex01 were never designed for modern macOS systems. Similarly, copying data to an ExFAT or NTFS drive risks stripping critical Apple metadata—data that can fundamentally alter investigative outcomes.
Apple Extended Metadata
Apple’s filesystems (APFS and HFS+) include Extended Metadata that tracks user behavior, system interactions, and file provenance in ways that Unix or Windows systems do not.
This includes attributes such as:- Last Used Date: A reliable timestamp showing the last time the user actually opened or interacted with a file or app.
- Finder Tags and Labels: Visual and organizational metadata often used in user workflows.
- Quarantine Flags: Indicators that a file was downloaded from the internet, including origin URLs and timestamps.
These attributes are stored and managed by macOS and are not preserved when data is imaged using third-party tools, copied to non-native filesystems, or interpreted using reverse-engineered forensic platforms.
A Real-World Metadata Example: When Time is Everything
Consider a case involving a departing employee who was not authorized to access sensitive files after a certain date. Suppose Unix “Access Time” metadata shows that the files in question were accessed several days after the employee’s departure. At first glance, this suggests a policy violation or even data theft.
However, on deeper inspection using a Mac-native forensic tool, the “Last Used Date” for those same files confirms they were not actually opened by the user after their departure. The Unix access time had been updated by a background service or indexing process—not the user.
This is a critical distinction. Relying on Unix Access Time alone could lead to incorrect accusations, flawed reporting, or inadmissible evidence. macOS uses the Last Used Date precisely because it better reflects user intent and interaction. Examiners must ensure their tools preserve and interpret this metadata accurately.
Final Thoughts: Image with Intention
Imaging Apple Silicon Macs is not just a matter of plugging in a tool and pulling data. It requires:- A clear understanding of the Mac’s security architecture.
- Valid authentication from the user—without which imaging is functionally impossible.
- The use of Mac-native tools and formats that respect and preserve Apple’s Extended Metadata.
- Avoiding legacy formats or non-native filesystems that could corrupt or omit critical data.
Getting this wrong doesn’t just compromise your evidence—it compromises your investigation. From inaccurate timelines to missing files, to faulty conclusions in your reports, improper imaging can have serious consequences in both legal and professional contexts.
At SUMURI, we’ve developed the tools and workflows to help examiners do this right. For a visual reference, we provide a free Apple Silicon Mac Imaging Flowchart that outlines the correct steps for modern forensic acquisition.
Proper imaging is foundational to digital forensics. With Apple Silicon Macs, it’s also more complex than ever. But with the right preparation, tools, and expertise, you can ensure no critical data is lost—and no investigation compromised.
- By Steve Whalen
- Categories: Blog, PALADIN


Why Use a Mac for Mac Forensics





